This is Part 1 of a series of blogs focussing on increasing adoption of Identity and Access Management (‘IAM’). The blogs will focus on the why, what and how of the IAM adoption journey.
Identity and Access Management (‘IAM’) is becoming an increasingly important part of digital transformation. COVID-19 has pushed many traditional organizations into the unknown territory of remote working – wherein, people work from outside their usual office network, accessing organizational resources as remote workers. At the end of day, all IT system users are just an identity – and the segregation between trusted and untrusted users is becoming blurred…
IAM is all about managing identity and access lifecycles across diverse IT systems. It broadly consists of three domains – Identity and Access Governance (‘IAG’), Access Management (‘AM’ – the term generally used for Single Sign On (‘SSO’) and Multi Factor Authentication (‘MFA’) functionalities) and Privileged Access Management (‘PAM’).
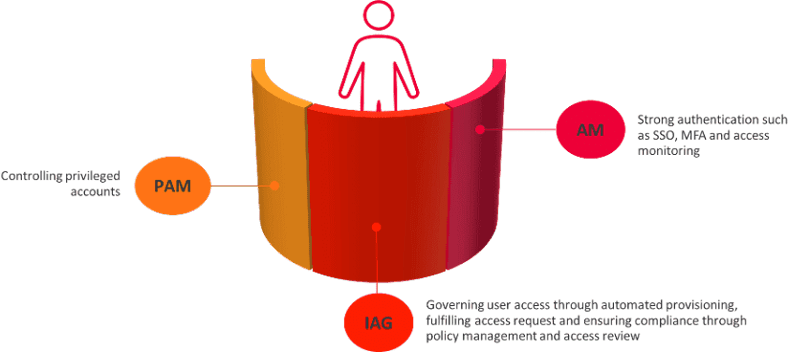
These three together ensure that the digital identities are managed in a secure and controlled manner.
While compliance is a big driver for adopting IAM, IAM systems also drive productivity in IT teams and enhance the end user experience for businesses. Some of the key challenges that an IAM system addresses are summarized in the figure below.
-min.png?width=788&height=325&name=7882-min%20(1)-min.png)
One of the other big drivers for IAM solutions is the complex and hybrid IT landscape. Most organizations have a large number of discreet IT systems – both on-premise as well as on cloud. Managing access across these IT systems is a huge challenge for any IT team – most organizations don’t have a clear visibility of all these access, let alone an ability to control them.
IAM solutions help address these challenges. Some of the stand out benefits include:
- Compliance – this is often the starting reason for most of the IAM projects. IAM solutions help improve the compliance posture of an organization.
- Need-based access: despite being one of the basic tenets of information security, this is also one of the most difficult to enforce. IAG solutions can help manage this requirement, through automated birth right provisioning together with approval based ad hoc access requests.
- Timely access removal: IAG solutions automate access removals based on information pulled from an authoritative source (typically HR and/or contractor management systems, also referred as the source of truth). This is applicable for both user movements as well as terminations.
- Visibility: IAM solutions provide visibility over what access users have across all IT systems. This also helps highlight orphan or duplicate user accounts. This is the foundation of any IAG system.
- Enforcing policies: IAM solutions help to enforce Segregation of Duties (‘SoD’) policies as well as other access policies (such as contractors not having access to certain systems)
- Controlling privileged access: PAM solutions control privileged access to IT systems by restricting the access as well as monitoring the privileged access sessions.
- Strong authentication: MFA solution helps enhance information security by requiring user to provide additional authentication based on defined policies.
- User experience – IAM makes access easy for end users. Whether it is the experience of requesting access, approving access requests or reviewing user accesses, user experience is another key driver for the acceleration towards IAM.
- Data quality: IAG solutions provide data sync features which ensure that user data (such as name, contact details, department, designation, etc) across various IT systems are always synced and up to date
- Simplified authentication: SSO solutions help users avoid having to individually authenticate on various IT systems.
- Approvals and reviews: Automation in IAG solutions makes it easier for approvers to approve access requests and reviewers to review user access (some IAG solutions also provide AI/ML features to help with this).
- Authentication issues: IAM solutions help with self-service password reset and account unlocking.
- First day access: IAG solution help ensure that the system access for a new user is ready when they join. This avoids productivity loss where in a new user spends their first few days (or weeks) just trying to get right access to the IT systems.
- Productivity – IAM solutions don’t just address the compliance and user experience challenges, but they also help drive the productivity of IT teams through automation. Features that enhance user experience almost always end up increasing user productivity too.
- Reduced helpdesk tickets: the self-service password reset and account unlocking results in fewer tickets being opened with the helpdesk.
- Productivity from day one: First day access allows users to be productive from day one.
- Data sync: Data sync features allow users to request for new access faster, without requiring duplicate data entries.
- Audit and compliance support: IT teams have to spend less time preparing for audits and other compliance activities such as regular access reviews. IAG provides multiple self-service features for both auditors as well as compliance teams.
- Automated provisioning: Finally, IAG takes away the routine user management activities and allows system administrators to focus on value adding activities.
These are the key factors behind why businesses are increasingly putting IAM at the centre of their digital journey. With increasing cyberattacks occurring around the world, security is paramount - and a good IAM solution ensures digital identities are secure while organization focuses on accelerating their digital transformation.
The next blog in this series will focus on the primary features of IAM solutions, so be sure to keep your eyes peeled…


